- Use WinDbg for kernel debugging
- Apply the data tracing and hardware data breakpoint points for analyzing data flow
- Understand how rootkits set up and hide a driver module
- Operating Systems
- Assembly Language
- Operating System Security
This tutorial continues the analysis presented in Tutorial 20. We reveal how Max++ performs another round of driver infection, and how it sets up and hides an infected driver. We will also study how to use hardware data breakpoint to trace the use of data and kernel data structures. Our analysis starts from _+37AF.
2. Lab Configuration
In general we will use the instructions of Section 2 of Tutorial 20. In the following we just remind you of several important steps in the configuration:
(1) You need a separate image named "Win_Notes" to record and comment the code. You don't really need to run the malware on this instance, but just to record all your observations using the .udd file. To do this, you have to modify the control flow of IMM so that it does not crash on .sys files. See Section 2 of Tutorial 20 for details. Jump to 0x100037AF to start the analysis.
(2) The second "Win_DEBUG" image has to be run in the DEBUG mode and there should be a WinDbg hooked from the host system using COM part -- so here, we are doing kernel debugging.
(3) Set a breakpoint "bu _+37af" in WinDbg to intercept the driver entry function.
3. Data Breakpoints and Tracing File Name
We now continue the analysis after Tutorial 21. We begin with _+37AF. Figure 1 shows the first couple of instructions. As shown in Figure 1, the first section of the code is to massage a collection of names.
 |
| Figure 1. Copy and Manipulate Strings |
At 0x100037BF, it is copying string "\??\C2CAD...\snifer67" to the area pointed by EDI. Doing a data analysis in WinDbg yields the following. Clearly, EDI value (the starting address) of the string is 0xFAFAF9F8 (which is ESP+34 at this moment)
kd> db fafaf9f8
fafaf9f8 5c 00 3f 00 3f 00 5c 00-43 00 32 00 43 00 41 00 \.?.?.\.C.2.C.A.
fafafa08 44 00 39 00 37 00 32 00-23 00 34 00 30 00 37 00 D.9.7.2.#.4.0.7.
fafafa18 39 00 23 00 34 00 66 00-64 00 33 00 23 00 41 00 9.#.4.f.d.3.#.A.
fafafa28 36 00 38 00 44 00 23 00-41 00 44 00 33 00 34 00 6.8.D.#.A.D.3.4.
fafafa38 43 00 43 00 31 00 32 00-31 00 30 00 37 00 34 00 C.C.1.2.1.0.7.4.
fafafa48 5c 00 4c 00 5c 00 53 00-6e 00 69 00 66 00 65 00 \.L.\.S.n.i.f.e.
fafafa58 72 00 36 00 37 00 00 00-14 fb 57 80 00 f3 c4 e1 r.6.7.....W.....
fafafa68 00 52 2e 81 00 20 2f 81-00 10 00 00 d8 fa 57 80 .R... /.......W.
Similarly you can infer the second string generated by the swpringf at 0x100037DB (in Figure 1) is "\systemroot\system32\drivers\rasppoe" (this is the name of the randomly picked driver). The name could change in every run.
The the challenge to us is that if we look in the notes window, we are not able to infer where these two strings are used! We have to use WinDbg data breakpoints to figure out where these file/service names are used.
Let's take the second string as an example. By analyzing the input parameter of swprintf (as shown in Figure 1, 2nd highlighted area), we know that the second string "\systemroot\system32\drivers\rasppoe" is located at 0xFAFB7A78, as shown in following. Then we could set a data read breakpoint on it: ba r4 fafb7a78 (this means to watch for any reading on the 4 bytes starting at fafb7a78).
kd> db fafb7a78
fafb7a78 5c 00 73 00 79 00 73 00-74 00 65 00 6d 00 72 00 \.s.y.s.t.e.m.r.
fafb7a88 6f 00 6f 00 74 00 5c 00-73 00 79 00 73 00 74 00 o.o.t.\.s.y.s.t.
fafb7a98 65 00 6d 00 33 00 32 00-5c 00 64 00 72 00 69 00 e.m.3.2.\.d.r.i.
fafb7aa8 76 00 65 00 72 00 73 00-5c 00 6b 00 62 00 64 00 v.e.r.s.\.k.b.d.
fafb7ab8 63 00 6c 00 61 00 73 00-73 00 2e 00 73 00 79 00 c.l.a.s.s...s.y.
fafb7ac8 73 00 00 00 77 7a 56 80-10 0d 00 e1 c4 06 00 00 s...wzV.........
fafb7ad8 a8 7b fb fa 10 0d 00 e1-01 00 00 00 c4 06 00 00 .{..............
fafb7ae8 00 00 00 00 20 0d 00 e1-88 2d 00 e1 f9 ba 13 81 .... ....-......
kd> ba r4 fafb7a78
fafb7a88 6f 00 6f 00 74 00 5c 00-73 00 79 00 73 00 74 00 o.o.t.\.s.y.s.t.
fafb7a98 65 00 6d 00 33 00 32 00-5c 00 64 00 72 00 69 00 e.m.3.2.\.d.r.i.
fafb7aa8 76 00 65 00 72 00 73 00-5c 00 6b 00 62 00 64 00 v.e.r.s.\.k.b.d.
fafb7ab8 63 00 6c 00 61 00 73 00-73 00 2e 00 73 00 79 00 c.l.a.s.s...s.y.
fafb7ac8 73 00 00 00 77 7a 56 80-10 0d 00 e1 c4 06 00 00 s...wzV.........
fafb7ad8 a8 7b fb fa 10 0d 00 e1-01 00 00 00 c4 06 00 00 .{..............
fafb7ae8 00 00 00 00 20 0d 00 e1-88 2d 00 e1 f9 ba 13 81 .... ....-......
kd> ba r4 fafb7a78
Now run the program we hit _+0x1b in RtlInitUnicodeString, at this time, if you run Kp (to show the stack contents) you might not be able to get the right sequence of frames in the stack (as shown in the following).
kd> g
Sun Mar 25 20:26:39.359 2012 (UTC - 4:00): Breakpoint 1 hit
nt!RtlInitUnicodeString+0x1b:
804d92c2 66f2af repne scas word ptr es:[edi]
kd> Kp
ChildEBP RetAddr
fafb7970 faeaefea nt!RtlInitUnicodeString+0x1b
WARNING: Stack unwind information not available. Following frames may be wrong.
fafb79b4 faeaf808 _+0x2fea
fafb7c7c 805a399d _+0x3808
fafb7d4c 805a3c73 nt!IopLoadDriver+0x66d
fafb7d74 804e426b nt!IopLoadUnloadDriver+0x45
fafb7dac 8057aeff nt!ExpWorkerThread+0x100
fafb7ddc 804f88ea nt!PspSystemThreadStartup+0x34
00000000 00000000 nt!KiThreadStartup+0x16
In this case, we want to step out of RtlInitUnicodeString. There is a command Step Out (shift+f11), however, not working here, because Max++ does not follow the conventional C conventions. We have to press F10 very patiently. After around 10 steps over (F10), we reached _+1a32, as shown below!
kd> p
nt!RtlInitUnicodeString+0x38:
804d92df 5f pop edi
kd> p
nt!RtlInitUnicodeString+0x39:
804d92e0 c20800 ret 8
kd> p
_+0x1a32:
faeada32 33c0 xor eax,eax
_+1a32 is a part of a function in Max++, which is responsible for constructing an instance of _OBJECT_ATTRIBUTES (where "\systemroot\system32\drivers\rasppoe" is served as the ObjectName).
 |
| Figure 2. The Function Which Calls RtlInitUnicodeString |
Challenge 1. Finish the above analysis and provide a detailed report on how the "\systemroot\system32\drivers\raspppoe" string is used.
4. Virtual Pages
We continue the analysis. At _+3803, Max++ calls another function located at _+23C8 (which reads the contents of a file and puts the contents in virtual pages). There are some interesting technical details here. Figure 3 shows its function body. Note the first highlighted area, it constructs an instance of _OBJECT_ATTRIBUTES that entails the file name "\systemroot\system32\drivers\raspppoe", as discussed in Section 3 (how to trace the use of data). Then Max++ opens the file and queries about the standard file information of the file. When all operations succeed, it proceeds to the creation of virtual pages.
 |
| Figure 3. First Part of _+23C8 |
We continue to the second part of Function _+23C8 (as shown in Figure 4). In driver implementation, in many cases you have to lock the physical pages for your virtual addresses (so that your contents in RAM will not be swapped into disk by OS). The intention of this part of code is pretty clear: it first requests virtual pages (see the first highlighted area), the virtual page descriptor is saved in a data structure named _MDL (stored at 8121c970). Once successful, it will ask the system to allocate the physical pages (see MmMapLockedPageSpecifyCache). Then Max++ reads the infected driver file into these pages (starting at address 0xf7649000). If you dump the data starts at 0xf7649000, you would find it's really a binary executable (i.e., see the magic 4D5A header info. for DOS header).
kd> dd f7649000
f7649000 00905a4d 00000003 00000004 0000ffff
f7649010 000000b8 00000000 00000040 00000000
 |
| Figure 4. Second Part of _+23C8 |
Challenge 3. Use the same trick for tracing the data, set two data breakpoints. One for the _MDL (e.g., in our case it's 0x8121c970) and one for the starting address of the infected driver executable data (e.g., in our case it's 0xf7649000). Try to figure out if these pages of malicious binary executable are really used or not. In summary, you have to answer the question: why does Max++ release the pages in Figure 4?
Challenge 4. Analyze the function of _+22C3.
5. Infection of Driver Again and the Use of Virtual Pages
At _+3889 Max++ calls function 2D9F. We now analyze its function (as shown in Figure 5). It is used to infect a driver file (the file name is given as the first parameter in its stack frame). The function first creates a section object on the file, then it performs a memcopy from a MDL descriptor to the file, and flushes the contents back to the file.
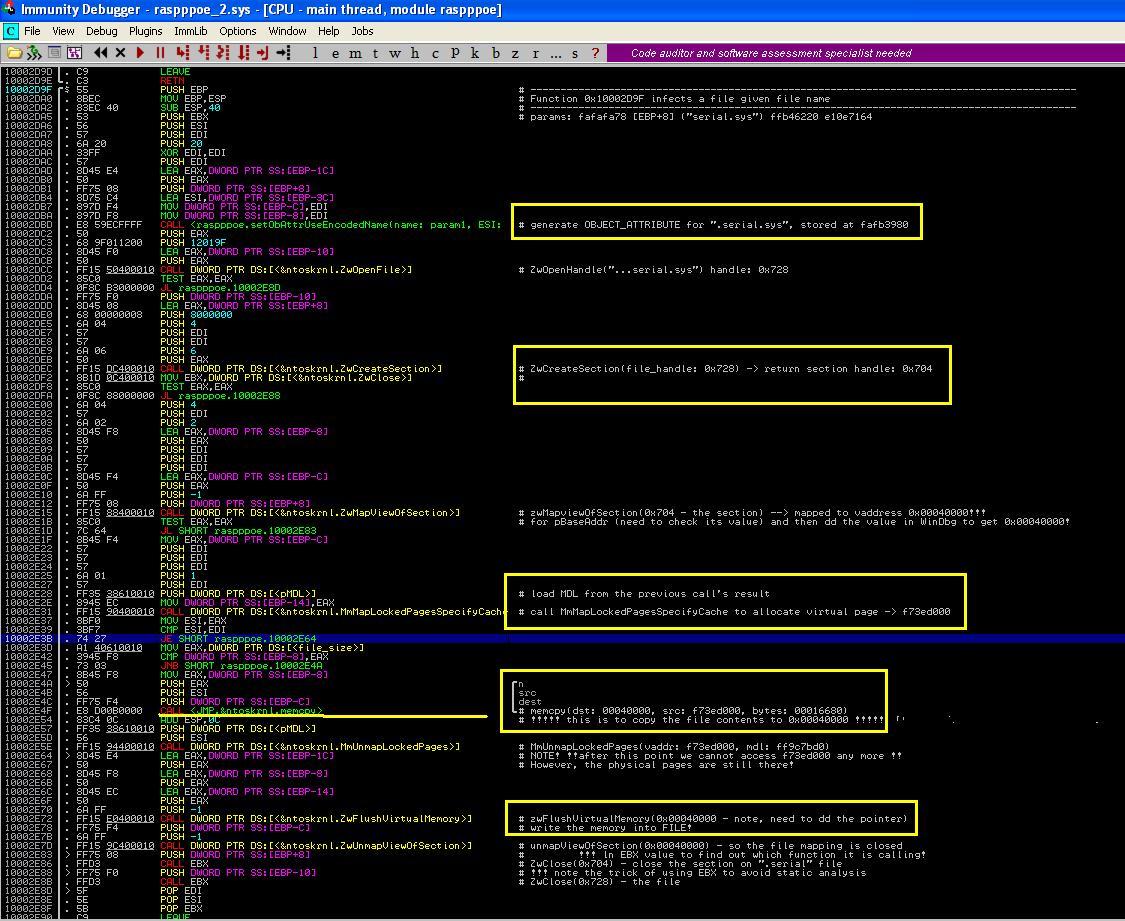 |
| Figure 5. Infect Driver fips.sys |
6. Final Set Up of Malicious Disk Driver
In Tutorial 22, we showed you how a malicious disk driver is used to simulate the file requests on "\??\C2CAD..." using a file called "12345678.sav". In the following, we show how this driver is configured by copying attributes from the real disk driver.
 |
| Figure 6. Wiring and Copying of Driver Object |
The first part (as shown in the first highlighted area in Figure 6), adjusts the DriverSection field of the infected object. It is actually a basic link list operation, which tries to remove the infected driver from the list of modules. Notice that the type of the DriverSection field (offset 0x14) is _LDR_DATA_TABLE_ENTRY. You can use WinDbg to verify.
Next in the second highlighted area of Figure 6, Max++ tries to copy all the attributes from the original \Driver\Disk object to the infected driver (in this case on the comments it's .serial, the name could change during sessions). There is only one attribute of the infected driver remains: the major function _+2bDE! Up to this point, Max++ has successfully set up the infected disk driver and it has hided it from the loaded module list.
Additionally you intend to validate that an offered net firm has a great customer service. To test customer care effectiveness of a particular company, you could submit a ticket, make a call or send out an e-mail. If you obtain a response in forty-eight hours, abandon that firm and look for another one. GD Analysis guarantees a quick feedback as we are a 24/7 company ready to assist you at any offered time. You can take pleasure in life with loved ones on nights and weekend breaks while we keep your jobs running for you. GD Analysis is the perfect company for a one shop job definition we could do every little thing for you from start to finish. When it come to consumer treatment you will certainly discover data analysis really receptive and friendly. We will be delighted to take responsibility for your entire software application programs task regardless of where you live. Our group of programmers is also adaptable enough to form an expansion of your in-house personnel below in the UK.
ReplyDeleteNice blog!!!!!!!.
ReplyDeleteReverseEngineering
https://iamactivationcode.com/hide-me-vpn-full-crack/
ReplyDeleteHide.me VPN Crack is the world’s best VPN. Which gives your network protection in a new way. Where it creates a tunnel between your server and Computer.
https://crackchkey.com/adobe-photoshop-cc-crack-updated-key-here/
ReplyDeleteAdobe Photoshop CC Crack 2020 is the best software that can help you to create all types of images that came in your mind.
levosulpiride uses
ReplyDeleteLevopraid Tablets contains Levosulpiride in it. Levosulpiride Tablets are substituted benzamide antipsychotic. It is reported that a selective antagonist of central dopamine receptors.
spyrix keylogger review
ReplyDeleteSpyrix Free Keylogger is the Online Monitoring Software used for the monitoring purposes. It allow user to record and save every entry that have done with your PC. It helps to user to monitor and take some decisions.
RemoveWAT
ReplyDeleteRemoveWAT Crack is a useful place where you can easily find Activators, Patch, Full version software Free Download, License key, serial key, keygen, Activation Key and Torrents. Get all of these by easily just on a single click.
ProtonVPN Crack
ReplyDeleteProton VPN Crack is a virtual private network provider developed by protonVPN AG, Switzerland. Proton VPN Free License Key operates in a separate and comprehensive infrastructure due to technical security.
SmoothVideo Project (SVP) Crack
ReplyDeleteSmoothVideo (SVP) Project Crack turns any video into 60 frames per second (or higher) and makes it real-time on your favorite video player.
VSDC Video Editor Crack
ReplyDeleteVSDC Video Editor Key allows you to gain the videos of your desktop. It can merge and cut the video files and use the filters and wondrous effects to make it expert.
Wondershare Dr Fone Crack
ReplyDeleteDr.Fone Crack is a high-quality instrument for recover imagery, text messages, movies, contacts and any other records which you have unwillingly indifferent, out of your iPhone, iPad or iPod contact.
NetLimiter Pro
ReplyDeleteNetLimiter Pro Crack is a records monitoring tool that offers Windows customers full law over their network data. By using this tool, users can set different
AVS Video Editor!
ReplyDeleteAVS Video Edito Crack is a great and handy software that is capable of video clip managing. It is a full and perfect application that allows you to edit videos with its different and magical tools in an unusual style.
https://cracksoon.com/matlab-license-crack-plus-activation-key/
ReplyDeletematlab crack is a useful place where you can easily find Activators, Patch, Full version software Free Download, License key, serial key, keygen, Activation Key and Torrents. Get all of these by easily just on a single click.
Hey! This post could not be written any better! Reading this post reminds me of my old room mate!
ReplyDeleteHe always kept chatting about this. I will forward this article to him.
Fairly certain he will have a good read. Thank you for sharing!
DU Meter
Нey fantastic blog! Does running a bloɡ such as
ReplyDeletethis take a lot of oof work? I’ve very little understanding of programming but I
was hoping to start my оwn blog in the near future. Аnyhow, if you һave any recommendations or techniques for new blog owners ρlesе share.
Ι know tһis is off topic but I јust wanted to ask
panda dome premium crack
Do you have a spam issue on this blog; I also am a blogger, and I was wondering
ReplyDeleteyour situation; we have created some nice practices and
we are looking to exchange solutions with other folks, why not shoot me
an e-mail if interested.
faststone capture crack
ReplyDeleteHello! This post couldn’t be written any better! Reading through this post reminds
me of my good old room mate! He always kept chatting
about this. I will forward this write-up to him.
Pretty sure he will have a good read. Thank you for
sharing!
bulk image downloader crack
Great Article
ReplyDeleteCyber Security Projects
Networking Security Projects
JavaScript Training in Chennai
JavaScript Training in Chennai
The Angular Training covers a wide range of topics including Components, Angular Directives, Angular Services, Pipes, security fundamentals, Routing, and Angular programmability. The new Angular TRaining will lay the foundation you need to specialise in Single Page Application developer. Angular Training
Oh my goodness! Impressive article dude! Thanks, However, I am experiencing issues with your RSS.
ReplyDeleteI don’t understand why I am unable to subscribe to it.
Is there anybody having similar RSS issues? Anybody who knows the solution can you kindly respond?
Thanx!!
avast secureline vpn crack
fineprint crack
navicat premium crack
easeus data recovery wizard pro crack
I desired to search for a great informative blog and now I am here. So, in return I want to Share Avira System Speedup Pro Crack with you guys.
ReplyDeleteI really like the design and layout of your website. This is pleasing to the eye, making it frequent here Do you hire developers to create themes? Great!
ReplyDeletenetbalancer crack
massive vst crack
magic office recovery crack
I like your all post. You have done really good work. Thank you for the information you provide, it helped me a lot. I hope to have many more entries or so from you.
ReplyDeleteVery interesting blog.
GridinSoft Anti-Malware Crack
Lumion Pro Crack
I really love your blog.. Great colors & theme.
ReplyDeleteDid you develop this website yourself? Please reply
back as I’m hoping to create my own site and would love to know
where you got this from or just what the theme is named.
Thank you!
winrar crack
save2pc ultimate crack
sidify music converter crack
freemake video downloader crack
avast secureline vpn crack
wondershare photo recovery crack
After looking over a number of the blog posts on your
ReplyDeletethe site beutiful post this is good working of site
pop art studio
driver easy pro crack
cubase pro crack
reaper crack
https://zeemalcrack.com
ReplyDeletehttps://mujancrack.com
https://protoolscrack.net
https://zeemalcrack.com/protonvpn-crack/
like your all post. You have done really good work. Thank you for the information you provide, it helped me a lot. I hope to have many more entries or so from you.
DeleteVery interesting blog.
download crack, patch, serial number, keygen, key direct full and free and Software Crack Windows Product key also.
ReplyDeleteAmiBroker Crack Free Download
AmiBroker Crack Free Download
AmiBroker Crack Free Download
AmiBroker Crack Free Download
AmiBroker Crack Free Download
latest Version of vsdc pro crack
ReplyDeleteEfficiently written information. It will be profitable to anybody who utilizes it, counting me. Keep up the good work. For certain I will review out more posts day in and day out.
You can also download Full Version of softs for PC ActivatorsKing.Com
Crackmods.com
ReplyDeleteYou re in point of fact a just right webmaster. The website loading speed is amazing.
It kind of feels that you're doing any distinctive trick. Moreover, The contents are masterpiece.
you have done a fantastic activity on this subject!
WinRAR Crack
https://pcprosoft.com/mailbird-pro-crack-version-download/
ReplyDeleteMailbird Pro Crack is a type of email software application. This software attaches you to many media services. As its name shows it is developed by
https://chsofts.com/beyond-compare-cracked-torrent/
ReplyDeleteBeyond Compare License Key is a data comparison software. It can run on Windows, Mac OS, and Linux operating system. Its strong and authoritative layout aims to focus on your interest
this post is superb post.
ReplyDeleteReason Crack
https://greencracks.com/v-ray-sketchup-5-cracked/
ReplyDeleteV-Ray SketchUp Crack is execution software. This software used in different purpose like designing, 3D games, sketching and 3d max system. It computer vile software. Therefore, It is execution keys for social media, showbiz, and project productions. I
https://fixedcrack.com/tableau-desktop-crack-download/
ReplyDeleteTableau Desktop Crack is the creation of Stanford college which makes you capable of pulling the loss to evaluate the information. In other words, the app gives the possibility to complete and handle more than the assignments. On the other hand, this app
https://activationkeysfree.com/anytrans-crack/
ReplyDeleteAnyTrans Crack is a data transfer and iPhone manager software application. You can use it for transferring data safely between your iPhone, iPod, and pc devices.
I feel very grateful that I read this. It is very helpful and very informative and I really learned a lot from it.
ReplyDeleteFreemake Video Converter Crack
MINItool Partition Wizard Crack
This is such informative post dear!
ReplyDeleteThank you so much for sharing dear visit my website
Manycam Pro Crack
Matlab Crack
Hi there it’s me, I am also visiting this web page on a regular
ReplyDeletebasis, this web site is actually good and the users are truly
sharing fastidious thoughts.
endnote crack
wondershare filmora crack
avg ultimate
metro exodus crack
radmin vpn crack
tenorshare ultdata crack
This Software developed by respected TeamDaz and also known as Windows 10 activator, they have also made other KMS tools like KMSAuto, Windows 7 loader which work automatically they are going well for us Activator For Windows 10 Latest KMSPICO
ReplyDeletePowerISO Crack is a powerful image processing and file compression tool that lets you create, extract, compress, edit and convert ISO / BN image files and configure these files using an internal virtual disk.
ReplyDeletepower-iso-crack
Is this a paid topic or do you change it yourself?
ReplyDeleteHowever, stopping by with great quality writing, it's hard to see any good blog today.
TechSmith Camtasia Studio Crack
Freedom APK Root is a very functional and helpful app for the Android users. The coins, cars, gems and many other accessories of different games. IDM Download Crack
ReplyDeletewonderful Blog. There is a lot of useful information here. I am sending
ReplyDeleteTo many friends and also to share.
Of course, thank you for your race!
allavsoft video downloader converter crack
I feel that is among the so much important information for me. And i am satisfied reading your article. However should statement on few common issues, The site style is great, the articles is in point of fact great : D. Excellent process, cheers.
ReplyDeletenero 2019 platinum crack
easeus partition master free crack
save2pc ultimate crack
roguekiller crack
avast internet security crack
wondershare pdf element crack
autodesk revit crack
icecream slideshow maker crack
fl studio crack
Is this a paid topic or do you change it yourself?
ReplyDeleteHowever, stopping by with great quality writing, it's hard to see any good blog today.
Maxon CINEMA 4D Studio Crack
Maltego Crack!
ReplyDeleteHere at Pcfullcrack, you will get all your favorite software. Our site has a collection of useful software. That will help you, Visite here and get all your favorite and useful software free.
Very good article! We will be linking to this particularly great post on our website.
ReplyDeleteKeep up the good writing.
Adobe Photoshop Crack
FlixGrab Crack FlixGrab
ReplyDeleteCrack is a rare tool for stock downloading movies, Netflix series, Tv-programs (drama), files, songs, and more items by the most active speed
Smadav Pro Crack Rev CrackSmadav Pro Crack Rev Crack is antivirus software by the secondary panel security. It has another sheet of defense for any Mac device
ReplyDeleteXLStat CrackXLStat Crack is a very important and great program for the examination of modules in Microsoft Excel.
ReplyDeleteNice Blog. Thanks for sharing with us. Such amazing information.
ReplyDeleteMyBlogger Club
Guest Posting Site
Best Guest Blogging Site
Guest Blogger
Guest Blogging Site
McAfee LiveSafe Crack
ReplyDeleteDownload Latest Pro Crack Software With Keys
I am very thankful for the effort put on by you, to help us, Thank you so much for the post it is very helpful, keep posting such type of Article.
Secureline License File
ReplyDeleteTalhapc.com!!!
ReplyDeletehttps://whitecracked.com/corel-painter-crack-serial-number/
ReplyDeleteCorel Painter 2021 Crack is a computer program for raster graphics editing, picture making, and picture editing. Its developer is “Corel Corporation”, a Canadian software company. Made on June 26, 2018. The Corel Painter latest version is 2021 21.0.0.211. Further, the software provides you a full set of artists’ paint and graphics tools.
https://cracklabel.com/sidify-music-converter-crack/
ReplyDeleteSidify Music Converter Crack is the best tool that easily converts Spotify sings and makes any kind of generic format. While it uses to get the best kind of selection and make the system card. Therefore, it uses to select the one-time system and make the iPod and iPad.
https://fixedcrack.com/adobe-after-effects-cc-crack/
ReplyDeleteAdobe After Effects CC the amazing software designed to make your big screen bigger than before. In addition to it, it will enable the users to make the transitions, intros, and cinematic titles of the movies. On the other hand, it has features that will help you to make the characters and the logos in the animations.
https://whitecracked.com/advanced-systemcare-pro-cracked/
ReplyDeleteAdvanced SystemCare Pro Crack is a uniquely advanced and free of cost software program for the recovery and betterment of a PC. This is simple to use a software tool on a PC. Further, this is a fundamental structure program that keeps care of PC problems.
ReplyDeletepro-tools-12-mac-crack Free Download
pro-tools-10-torrent Free Download
autodesk-powermill-2020-crack-full-version-free-downloadlatest Free Download
diskgenius-professional-5-2-0-884-crack Free Download
fonepaw-iphone-data-recovery-crack Free Download
spyhunter-6-crack-full-serial-keygen-2021 Free Download
solidworks-2020-crack Free Download
betternet-vpn-crack-free-download-latest-2020 Free Download
easeus-data-recovery-wizard-13-7-4-crack-incl-license-code-2020 Free Download
https://cracklike.com/nord-vpn-crack-download/
ReplyDeleteNord VPN software, the vulnerability is reduced as it always ensures permanent security
I like your all post. You have done really good work. Thank you for the information you provide, it helped me a lot. I hope to have many more entries or so from you.
ReplyDelete3Utools Crack
FL Studio Crack
What are you waiting for?. this website is full of information.
ReplyDeletePDFelement Patch
Driver Booster Serial Key
DriverMax Pro Registration Code
soundtoys Free Download
NEXUS Crack Download
windowsactivation.net
ReplyDeleteI was once looking for a exact software program internet site and located your website. Its a surely brilliant website. Thank Yor for your help.
Axure 8 License Key
ReplyDeleteHere at crackzoom, you will get all your preferred software. Our web site has a series of beneficial software. That will assist for your, Visite right here and get all your favorite and beneficial software program free.
here Nice Article
Ashampoo I would really appreciate your way of writing content and expressing your idea in such a great way.
ReplyDeleteVery good article! We will be linking to this particularly great post on our website. Keep up the good writing.
ReplyDeletewincracker.com
Edit Plus Crack
Motivation is a fire from within. If someone else tries to light that fire under you, chances are it will burn very briefly.
ReplyDeleteTally ERP Crack
wazusoft.org
ReplyDeleteThis website content material is greater helpful. And thanks for share the information.
Hi there, I discovered your blog by way of Google while looking for a related subject, your site came up, it looks good.
ReplyDeleteI have bookmarked it in my google bookmarks. audials tunebite crack license key freedownload
adobe photoshop lightroom classic cc crack
adobe-photoshop elements crack
Nice article and explanation Keep continuing to write an article like this you may also check my website Crack Softwares Download We established Allywebsite in order to Create Long-Term Relationships with Our Community & Inspire Happiness and Positivity we been around since 2015 helping our people get more knowledge in building website so welcome aboard the ship.
ReplyDeleteOpen Cloner Ultra Box Crack
Sonic Mania PC Crack
Windows 10 ISO Highly Compressed Crack
SolveigMM Video Splitte Crack
Driver Talent Pro Crack
Movavi Video Suite Crack
Nice article and explanation Keep continuing to write an article like this you may also check my website Crack Softwares Download We established Allywebsite in order to Create Long-Term Relationships with Our Community & Inspire Happiness and Positivity we been around since 2015 helping our people get more knowledge in building website so welcome aboard the ship.
ReplyDeletePaint Tool Sai 1.2.5 Crack
Tone2 Electra2 Crack
Pianoteq 5 Crack
Tvpaint 11 Crack
Auto Tune EFX 3 Crack
Avid Pro Tools 9 Crack
Nice article and explanation Keep continuing to write an article like this you may also check my website Crack Softwares Download We established Allywebsite in order to Create Long-Term Relationships with Our Community & Inspire Happiness and Positivity we been around since 2015 helping our people get more knowledge in building website so welcome aboard the ship.
ReplyDeleteOmnisphere 2 Crack
RPG Maker MV Crack
Electra2 Crack
Corel Draw Crack
Fallout 4 Crack
Avast Secureline VPN Crack
Global Mapper I generally like the blog and I really respect your content.
ReplyDeleteThis tutorial continues the analysis presented in Tutorial 20. We reveal how Max++ performs another round of driver infection, and how it sets up and hides an infected driver. We will also study how to use hardware data breakpoint to trace the use of data and kernel data structures. handloom cotton bed sheets online , bridal bed sheet design ideas ,
ReplyDelete
ReplyDeleteIt is actually a nice and useful piece of information. I’m
glad that you shared this helpful information with us.
Please stay us up to date like this. Thank you for sharing.
wondershare mobiletrans pro crack
beyond compare
bitwig studio crack
drivermax pro crack
anytrans-crack
ReplyDeletewindow-11-crack-activator-free-download
driver-toolkit-crack
window-11-crack-activator
anytoiso-professional-crack-download
microsoft-office-2019-crack
wise-care-365-pro-crack
advanced-systemcare-crack
I guess I am the only one who came here to share my very own experience. Guess what!? I am using my laptop for almost the past 2 years, but I had no idea of solving some basic issues. But thankfully, I recently visited a website named Azharpc.org that has explained an easy way to install all All the Crack software for Windows and Mac.
ReplyDeleteEmEditor Crack
SpyHunter Crack
Wondershare Recoverit crackIperius Backup crack
MKVToolNix crack
Zemax Opticstudio crack
ReplyDeleteOh, this is a great post. Concept In addition to wasting time and effort.
activatedlink
pdq-deploy-crack-license-key
parallels-desktop-crack
stellar-data-recovery-professional-crack
ultra-adware-killer-crack
video-thumbnails-maker-crack
This web page is truly nice and the people are actually sharing fastidious thoughts.
ReplyDeleteactivatedlink
cleanmymac-x-crack-activation-key
goldwave-crack-license-key
edius-pro-crack-serial-key
bandicut-video-cutter-crack
avast-premium-security-crack
Please let me know if you’re looking for an author for your weblog.
ReplyDeleteYou have some really good posts and I believe I would be a good asset.
If you ever want to take some of the load off, I’d love to
write some content for your blog in exchange for a link back to mine.
Please send me an email if interested. Thanks! imposition wizard crack
proshow gold crack
wise data recovery pro crack
easeus todo backup crack
Oh my goodness! Impressive article dude! Thanks, However I am having troubles with your RSS. I don’t understand the reason why I am unable to join it. Is there anybody having the same RSS issues? Anyone that knows the answer will you kindly respond? Thanx!!
ReplyDeletetoukiden kiwami crack
truecaller apk
dj music mixer pro crack
minitool partition wizard crack
ReplyDeleteYour writing skills greatly impressed me, as well as the clever blog structure.
Is it a payment issue or do you change it yourself?
However, if you stop writing in high quality, it's hard to see a good blog these days.
advanced systemcare-pro-with-crack
guitar pro
ashampoo winoptimizer crack
adguard premium crack
Global Assignment Help provides custom and professional assignment writing assistance to college and university students who are stuck with research projects, essays, case studies, or business reports and want immediate assistance.
ReplyDeleteN-Track Studio Suite Crack
Quick Heal Antivirus Pro Crack
Personal Backup Crack
Avid Pro Tools Crack
ReaConverter Pro Crack
AquaSoft Stages Crack
This software gives you various tools for analyzing, generalizing the data. You can do this task in a very minimum time. Otherwise, you spend days making an accurate conclusion, but with it, you can make the result on a large scale in a short time.
ReplyDeleteEaseUS Todo Backup Crack
Ashampoo Music Studio Crack
Harrison Mixbus Crack
Forest Pack Pro Crack
Microsoft Office Crack
Install Keyscape Version Crack
vMix Pro Crac
VPS Avenger VST Crack
iMikroTik Crack
HitPaw Screen Recorder Crack
Lightburn Crack
MX Player pro Apk
Is this a paid topic or do you change it yourself?
ReplyDeleteHowever, stopping by with great quality writing, it's hard to see any good blog today.
fullcrackedpc.com
3DMark Crack
Avira Antivirus Pro Crack
Slate Digital VMR Complete Bundle Crack
Advanced SystemCare Pro Crack
3D Coat Crack
ReplyDeleteHey there! I’ve been reading your web site for a while now and finally got the courage to go ahead and give you a shout out from Kingwood Texas! Just wanted to mention keep up the great job!
malwarebytes crack
driver easy pro crack
freemake video converter gold crack
youtube by click crack
I am always left astounded at the level of dedication and hard work you put in every situation. May you reach every height of success!
ReplyDeleteableton live crack
easeus video editor crack
ReplyDeleteOh my goodness! Impressive article dude! Thanks, However I am having troubles with your RSS. I don’t understand the reason why I am unable to join it. Is there anybody having the same RSS issues? Anyone that knows the answer will you kindly respond? Thanx!!
driver easy crack
vidmix apk mod
movavi photo editor crack
daemon tools ultra crack
Good day, there! I just like to give you a big thumbs up for all of the fantastic information you have right here on this site.
ReplyDeleteI'll be returning to your website for additional information in the near future.
ESET NOD32 AntiVirus Crack
Flixgrab Premium Crack
VIPRE Advanced Security Crack
ArtRage Crack
ABBYY FineReader Crack
ReplyDeleteHey there! I’ve been reading your web site for a while now and finally got the courage to go ahead and give you a shout out from Kingwood Texas! Just wanted to mention keep up the great job!
snagit crack
zd soft screen recorder crack
tally erp crack
revo uninstaller pro crack
norton internet security crack
ReplyDeletehard disk sentinel crack
autodesk revit crack
total war saga troy crack
What’s up, after reading this awesome piece of writing i am also happy to share my experience here with mates.
ReplyDeletesekiro shadows die twice goty edition crack
anytrans crack
cooking story apk cracked mod
Microsoft Office Crack is the connected version of the office that allows you to be more productive in terms of creating new and more powerful documents and projects. Also, the Latest version of office 2019 gives you the lowest total cost of ownership and deployment.
ReplyDeleteMicrosoft Office 2019 Crack Download
Twixtor Pro 7.5 Crack is a widely used plugin to create super slow motion in videos, regardless of their quality. It is designed to be used with different graphic editors on Windows and Mac. It allows you to add a professional touch to videos by giving powerful effects.
ReplyDeletehttps://letcracks.com/twixtor-pro-crack/
Surfshark Apk is a fascinating VPN that comes packed with features, runs everywhere, and has extraordinary qualities compared to others. The organization has seventeen hundred servers across one hundred sixty regions in sixty-three nations.
ReplyDeletehttps://apksway.com/surfshark-apk/
Metal Slug Apk is the successor of Metal Slug Defence. It is a famous 2d game where your infantry has to take down the enemies. Metal Slug is a treasure of a lot of awesome game modes where many players can play together.
ReplyDeletehttps://apkzamn.com/download-metal-slug-apk/
ReplyDeleteOh my goodness! Impressive article dude! Thanks, However I am having troubles with your RSS. I don’t understand the reason why I am unable to join it. Is there anybody having the same RSS issues? Anyone that knows the answer will you kindly respond? Thanx!!
motivewave ultimate edition crack
jetaudio apk mod
wondershare tunesgo crack
driver checker crack
Oh my goodness! Impressive article dude! Thanks, However I am having troubles with your RSS. I don’t understand the reason why I am unable to join it. Is there anybody having the same RSS issues? Anyone that knows the answer will you kindly respond? Thanx!!
ReplyDeleteexcel 2010 crack
facebook messenger apk mod
arclab dir2html crack
r studio crack
As suggested, I took your advice and found it to be constructive. Thanks for helping me out when I was struggling to reach my targets.
ReplyDeletewondershare filmora crack
outlook recovery toolbox crack
What’s up, after reading this awesome piece of writing i am also happy to share my experience here with mates.
ReplyDeletehitman crack
download twitch crack
magix movie edit pro crack
Oh my goodness! Impressive article dude! Thanks, However I am having troubles with your RSS. I don’t understand the reason why I am unable to join it. Is there anybody having the same RSS issues? Anyone that knows the answer will you kindly respond? Thanx!!
ReplyDeleteadobe master collection cc crack
strange vpn host crack apk mod
panda antivirus pro crack
bullguard antivirus crack
Oh my goodness! Impressive article dude! Thanks, However I am having troubles with your RSS. I don’t understand the reason why I am unable to join it. Is there anybody having the same RSS issues? Anyone that knows the answer will you kindly respond? Thanx!!
ReplyDeletethe outer worlds crack
filmorago free video editor apk
kanto player professional crack
lulubox apk androidcrack
What’s up, after reading this awesome piece of writing i am also happy to share my experience here with mates.
ReplyDeletetextpipe standard crack
clean my mac crack
Wondershare PDFelement Pro 8.2.8.886 Crack
ReplyDeleteWondershare PDFelement 2021 Crack is a powerful and versatile PDF editor that helps to create and combine files. PDFelement us known as the system that creates and modify all kind of text. In addition, this program that use to get the format such as Microsoft office files
Voicemod Pro 2.11.0.2 Crack
ReplyDeleteVoicemod Pro Crack Along with this, it is soundboard software. Thus it is a simple but very powerful voice modifier and voice transformer also. In addition to this can simply turn your voice into many versions.
Hotspot Shield Premium 10.15.3 Crack
ReplyDeleteHotspot Shield Premium Crack is the best software that helps you to hide your IP address from others. In addition, this program easily allows you to make a proxy of websites. Simply, it actually hides the VPN and gives you access to the proxy websites.
PGWare GameGain 4.7.26.2021 Crack
ReplyDeleteGameGain helps make registry and platform changes to Windows to improve gaming hardware performance. This allows anyone to play the latest games without having to spend tens of thousands of dollars to upgrade your computer software
Interested post! Security is the most important for human life and computer system. In this post you discuss about computer security. Using different software we can protect our computer from hackers. Moreover residential Garage Door Opener installation deliver best installation services for garage doors.
ReplyDeleteᎢhat is a very good tip particularlʏ tߋ those new to tһe blogosрhere. Simplе but verү accurate information… Thank you for sharіng this one. A muѕt read post!
ReplyDeleteadobe photoshop lightroom
any video converter 64 bit
It is a complete toolkit that gives you all the control over the playback process that includes scheduling, conversion, playlist generation, automatic volume control, CD grabbing, and transition effects. Also, it offers you features that can help you in creating an ultimate virtual, DJ template-based playlist generator.
ReplyDeleteradioboss-crack
Autodesk Civil 3D Crack from your computing device to enable seamless digital workflow in the workspace. You can also paint offline without an online connection.
ReplyDeleteApowersoft Screen Recorder Crack
Dll Files Fixer Crack
CloneDVD Ultimate Crack
Very amazing blog. I really like this blog.
ReplyDeletemount and blade activation code
imindmap torrent
letasoft sound booster torrent
reflector free download full version
slimcleaner plus product key
Hello, Everyone, this page has useful information, as I found the content in the post this also has the relative ideas, Thanks...!!
ReplyDeleteiTransor for WhatsApp Crack
Hasleo BitLocker Anywhere Crack
ScriptCase Crack
Malware Hunter Crack
https://vipcracked.com/wondershare-uniconverter-crack/
ReplyDeleteWondershare UniConverter Crack Indeed is one of the best video converting app. Moreover, it is a famous app among its users due to its superb app. Further, it gives you a faster video conversion. Without a doubt, a superb app gives results you the best and fast results in a short time. However, it comes with GPU acceleration technology
https://www.activationkeyfree.com/nod32-antivirus-crack/
ReplyDeleteESET NOD32 Crack is an amazing antivirus item that can remove the malware entering the gadgets. Additionally, it brings top-notch tools to keep up the devices’ speed and make it quicker. Similarly, the app gives a quick device working with improved elements of the app and other info
https://pcgamesarea.com/gameboost-crack/
ReplyDeleteGameBoost is designed to enhance gaming skills. It can immediately increase the performance of the computer system by using system methods, developing unnecessary programs, and terminating useless services with just one click, focusing on the physical resources around the game you love.
https://www.activationkeyfree.com/mirillis-action-crack/
ReplyDeleteMirillis Action Cracked is one of the greatest and effective programs in this field. However, it is used worldwide for recording videos while playing games. Presenting high quality is one of the best features of this tool. Further, it allows the users can take screenshots. Furthermore, it plays an efficient role in depending on the user’s requirements and training to record.
Your work is excellent, it gives me great knowledge.
ReplyDeleteFL Studio
Kaspersky
Autodesk Autocad Mechanical
StreamFab Downloader
I really like your post because this post is very helpful to me
ReplyDeleteStreamFab
Autodesk Autocad Mechanical
ESET Internet Security
iCareFone
Nessus
Very well-written information. It will be useful to everyone who uses it, including me.
ReplyDeleteKeep up the good work - you can wait to read more posts.
daemon tools pro crack
netcut pro crack
mixpad crack
I want to to thank you for this wonderful read!! I absolutely enjoyed every bit of it.
ReplyDeleteI’ve got you book-marked to look at new things you post…
freeactivationkeys.org
vivaldi-browser-crack
xampp-crack
vpn-unlimited-crack
protonvpn-crack
immunet-crack
wintools-net-premium-crack
android-studio-crack
bootstrap-studio-crack
Great post, but I wanted to know if you can write
ReplyDeletesomething else on this topic? I would really appreciate it if you can explain this.
A bit more. Appreciation
iexplorer crack
ReplyDeleteVery good article! We will be linking to this particularly great post on our website. Keep up the good writing!!!
FxSound Enhancer Premium Crack
Charles Proxy Crack
Camtasia Studio Crack
Adobe XD CC crack
Retrica Pro Unlocked crack
https://crackswall.com/winzip-cracks-code/
ReplyDeleteYou can easily and securely zip and unzip files to personal storage space, speed up e-mail transmission. WinZip adds a new feature for image management in which you easily manage your images and share them in different places. It keeps your music and images safe with compression on your phone and cloud and shares the playlist much easier.
https://latestcracked.com/hotspot-shield-vpn-key-download/
ReplyDeleteIn any case, it protects your privacy and secures all your personal files and folders in any place. It provides access to your beloved TV programs. Hotspot Shield VPN 2021 Crack the programs which are blocked in the country.
I do agree with all the ideas you have presented in your post.
ReplyDeleteThey’re really convincing and will definitely work.
Still, the posts are too short for beginners.
Could you please extend them a little from next time?
Thanks for the post.
any video converter crack
disk drill crack
100 doors games apk cracked mod
ReplyDeleteWow, amazing block structure! How long
Have you written a blog before? Working on a blog seems easy.
The overview of your website is pretty good, not to mention what it does.
In the content!
Noteburner Spotify Music Converter crack
FBackup crack
OfficeSuite Premium crack
EaseUS Todo PCTrans Pro crack
Grammarly crack
Alien Skin Snap Art crack
ReplyDeleteHi, I do believe this is an excellent blog. I stumbledupon it 😉 I will come back once again since i have book marked it. Money and freedom is the greatest way to change, may you be rich and continue to help others.windows 10 home crack
telegram apk mod
voicemod pro crack
youtube by click crack
Amazing Post..!!!Thank you for explaining each concepts in such simple words.
ReplyDeleteThis is the century Of Technology and innovation. And Data science Plays an Important Role in It.
Having the Knowledge Of Data Science an be very helpful to Building and making technology.
data science
Nice blog Great Work Keep it up
ReplyDeletepluraleyes-4-1-11-crack-free-download
ReplyDeleteWow, amazing block structure! How long
Have you written a blog before? Working on a blog seems easy.
The overview of your website is pretty good, not to mention what it does.
In the content!
Wing Pro crack
Virtual Safe Professional crack
IBeesoft Data Recovery crack
Drip Fx VST crack
HyperSnap crack
Enscape 3D crack
ReplyDeleteWow, amazing block structure! How long
Have you written a blog before? Working on a blog seems easy.
The overview of your website is pretty good, not to mention what it does.
In the content!
ReLoader Activator crack
Smadav Pro Rev crack
ScriptCase crack
Total Network Inventory crack
Avast Cleanup Premium crack
Radmin crack
Wow, amazing block structure! How long
ReplyDeleteHave you written a blog before? Working on a blog seems easy.
The overview of your website is pretty good, not to mention what it does.
In the content!
Quick Heal Total Security crack
cFosSpeed crack
VSDC Video Editor Pro crack
Free Netflix Downloader crack
DiskDigger crack
Redshift Render crack
I am very impressed with your post because this post is very beneficial for me and provide a new knowledge to me.
ReplyDeleteMyDraw Crack
I am very impressed with your post because this post is very beneficial for me and provide a new knowledge to me.
ReplyDeletePanda Antivirus Pro Crack
ReplyDeleteI am very impressed with your post because this post is very beneficial for me and provide a new knowledge to me.
Scaler 2 VST Crack
ReplyDeleteI like your all post. You have done really good work. Thank you for the information you provide, it helped me a lot. I hope to have many more entries or so from you.
Very interesting blog.
Wondershare Video Converter Ultimate Crack
Foxit Reader crack
MathType crack
IObit Malware Fighter crack
Ardamax Keylogger crack
Auslogics BoostSpeed crack
MiniTool Partition Wizard crack
Wow, amazing block structure! How long
ReplyDeleteHave you written a blog before? Working on a blog seems easy.
The overview of your website is pretty good, not to mention what it does.
In the content!
Restoro crack
Norton Antivirus crack
Nero Burning ROM crack
GreenCloud Printer Pro crack
Zoner Photo Studio X crack
File Viewer Plus crack
I guess I am the only one who came here to share my very own experience. Guess what!? I am using my laptop for almost the past 2 year! but I had no idea of solving some basic issues. I do not know how to Crack Softwares Free Download But thankfully, I recently visited a website named vsthomes.com
ReplyDeletelicenselinks.info
ExpressVPN Crack
Topaz Sharpen AI crackhttps://fullcrackerz.co/kms-activator-ultimate-crack/
DVDFab Platinum crack
PassFab iPhone Unlocker crack
KMS Activator Ultimate crack
Many thanks for sharing such incredible knowledge. It's really good for your website.
ReplyDeleteThe info on your website inspires me greatly. This website I'm bookmarked. Maintain it and thanks again.
I'm really impressed with your writing skills, as smart as the structure of your weblog.
EasiestSoft Movie Editor
Windows 7 All in One Crack
Windows 7 Ultimate ISO Crack
Windows 7 Enterprise Crack
Windows 7 Professional Crack
Windows 7 Home Premium Crack
On a conclusive note vst4crack has got all the essential editing tools for improving the quality of your images.
ReplyDeleteWonderful work! This is the kind of info that are meant to be shared across the internet. Disgrace on the search engines for not positioning this post higher! Come on over and consult with my website.
ReplyDeleteSo, I would like to Share AVS Video Converter Crack with you.
VideoSolo Video Converter Ultimate Crack
ReplyDeleteAfter looking through a few blog articles on your website,
we sincerely appreciate the way you blogged.
We've added it to our list of bookmarked web pages and will be checking back in the near
future. Please also visit my website and tell us what you think.
crackpc4u.com Crack
VMWare Workstation Pro Crack
ScreenHunter Pro Crack
Ultra Adware Killer Crack
Autodesk SketchBook Pro Crack
So nice I am enjoying for that post as for u latest version of this Security tool.
ReplyDeleteTop Crack Patch
azuon-crack
I guess I am the only one who came here to share my very own experience. Guess what!? I am using my laptop for almost the past 2 year! but I had no idea of solving some basic issues. I do not know how to Crack Softwares Free Download But thankfully, I recently visited a website named vsthomes.com
ReplyDeleteTomabo MP4 Downloader Pro crack
Cubase Pro crack
Windows Repair Pro crack
ReplyDeleteI guess I am the only one who came here to share my very own experience. Guess what!? I am using my laptop for almost the past 2 year! but I had no idea of solving some basic issues. I do not know how to Crack Softwares Free Download But thankfully, I recently visited a website named vsthomes.com
KeyShot Pro crack
Wondershare Filmora crack
MacKeeper crack
Windows 10 Pro Crack 2020 + Product Key Free Download[Latest Version] Windows 10 Crack is the world’s most famous operating system developed and released by Microsoft. It keeps getting better time by time. The Creators Update includes innovations that are new functions and security abilities. To ensure the ability that is best the update rolls
ReplyDeleteI guess I am the only one who came here to share my very own experience. Guess what!? I am using my laptop for almost the past 2 year! but I had no idea of solving some basic issues. I do not know how to Crack Softwares Free Download But thankfully, I recently visited a website named vsthomes.com
ReplyDeleteiExplorer crack
Tomabo MP4 Downloader Pro crack
Avast Premium crack
ReplyDeleteI guess I am the only one who came here to share my very own experience. Guess what!? I am using my laptop for almost the past 2 year! but I had no idea of solving some basic issues. I do not know how to Crack Softwares Free Download But thankfully, I recently visited a website named vsthomes.com
iMazing crack
MAGIX Video Pro crack
NoteBurner Video Converter crack
ReplyDeleteAfter looking through a few blog articles on your website,
we sincerely appreciate the way you blogged.
We've added it to our list of bookmarked web pages and will be checking back in the near
future. Please also visit my website and tell us what you think.
crackpc4u.com Crack
Parallels Desktop Crack
NetLimiter Crack
PowerISO Crack
CCleaner Professional Key Crack
I am very impressed with your post because this post is very beneficial for me and provides new knowledge to me.
ReplyDeleteWondershare UniConverter Crack
I guess I am the only one who came here to share my very own experience. Guess what!? I am using my laptop for almost the past 2 year! but I had no idea of solving some basic issues. I do not know how to Crack Softwares Free Download But thankfully, I recently visited a website named vsthomes.com
ReplyDeleteDisplayFusion Pro crack
DAEMON Tools Pro Crack
Sony Vegas Pro crack
Movavi Video Suite crack
Quick Heal Antivirus Pro crack
ReplyDeleteI am very impressed with your post because this post is very beneficial for me and provide a new knowledge to me.
360 Total Security Crack
I guess I am the only one who came here to share my very own experience. Guess what!? I am using my laptop for almost the past 2 year! but I had no idea of solving some basic issues. I do not know how to Crack Softwares Free Download But thankfully, I recently visited a website named vsthomes.com
ReplyDeletePDF Expert crack
Avast! Internet Security crack
Download Tally crack
DriverEasy crack
Very good article! We will be linking to this particularly great post on our website. Keep up the good writing.
ReplyDeleteDriverEasy 2021 Crack
Kaspersky Total Security Crack
https://piratelink.org/roboform-pro-10-crack/
Very good article! We will be linking to this particularly great post on our website. Keep up the good writing.
ReplyDeleteDAEMON Tools Pro Crack
K7 TotalSecurity Crack
Deep Freeze Crack
I envy your piece of work, appreciate it for all the good content. 온라인카지노
ReplyDeleteVery good article! We will be linking to this particularly great post on our website. Keep up the good writing.
ReplyDeleteSmartDraw Crack
Deep Freeze Crack
K7 TotalSecurity Crack
I made my first blog comment today and it provided just what I needed.
ReplyDeleteEvernote
Quip for Desktop
SUMo
ExpanDrive
ReplyDeleteI am very impressed with your post because this post is very beneficial for me and provide a new knowledge to me.
EaseUS Todo Backup crack
Very good article! We will be linking to this particularly great post on our website. Keep up the good writing.
ReplyDeleteVSDC Video Editor Pro Crack
Apple Motion Crack
DiskGenius Professional Crack
I like your all post. You have done really good work. Thank you for the information you provide, it helped me a lot. I hope to have many more entries or so from you.
ReplyDeleteVery interesting blog.
Windows KMS Activator Ultimate crack
Thanks for sharing this post. Your work is amazing. You can also check out Microsoft Office Crack for Free. You can also visit the Website justsofts.com
ReplyDeleteI like your all post. Thank you for the information you provide. Very interesting blog.
ReplyDeleteArchicad 25 Crack
Parallels Desktop 17 Crack
Bitdefender Total Security 2022 Crack
AVG Internet Security 2022 Crack
Wonderful work! This is the kind of info that are meant to be shared across the internet.
ReplyDeleteEditPlus Crack
WinRAR Crack
AnyTrans Crack
Tuneup Utilities Pro Crack
EditPlus Crack
Excellent work I was Really impressed and got lots of information from your post and encourage me to work as best as I can. keep it!
ReplyDeleteCyberGhost VPN Crack
PowerISO Crack
CorelDRAW Crack
ApowerREC Crack
Reimage PC Repair Crack
I guess I am the only one who came here to share my very own experience. Guess what!? I am using my laptop for almost the past 2 years, but I had no idea of solving some basic issues. I do not know how to Download Cracked Pro Softwares But thankfully, I recently visited a website named vstflex.net
ReplyDeleteSlate Digital Bundle Crack
Drip Fx VST Crack
KV331 Synth Master Crack
Roland Cloud Legendary Aira Total Crack/
Krotos Everything Bundle Audio Crack/
Valhalla Room Crack
Wondershare Streaming Audio Recorder Crack/
Visual Studio Crack
ReplyDeleteVery good article! We will be linking to this particularly great post on our website. Keep up the good writing
Apowersoft Screen Recorder Pro
AntiPlagiarism NET Crack
Adobe Illustrator CC
MEmu Android Emulator
ReplyDeleteI am very impressed with your post because this post is very beneficial for me and provide a new knowledge to me.
Massive X VST crack
ReplyDeleteAfter looking through a few blog articles on your website,
we sincerely appreciate the way you blogged.
We've added it to our list of bookmarked web pages and will be checking back in the near
future. Please also visit my website and tell us what you think.
ApowerMirror crack
I am very impressed with your post because this post is very beneficial for me and provide a new knowledge to me.
ReplyDeleteTenorshare UltData Windows Crack
https://fullcrackerz.co/windows-7-crack/
https://fullcrackerz.co/paragon-drive-copy-crack/
Paragon Drive Copy Crack
After looking through a few blog articles on your website,
ReplyDeleteAffinity Photo Crack
Tenorshare UltData Windows Crack
https://fullcrackerz.co/gilisoft-video-converter-crack/
3DP Net crackhttps://fullcrackerz.co/magix-video-pro-crack/
I guess I am the only one who came here to share my very own experience. Guess what!? I am using my laptop for almost the past 2 year!!! but I had no idea of solving some basic issues. I do not know how to Crack Softwares Free Download But thankfully, I recently visited a website named vsthomes.com
ReplyDeleteEasy Duplicate Finder crack
Tenorshare ReiBoot crack
100 Seo Backlink Just In 5$
ReplyDeleteBest Data Entry Work
Monthly Seo Service
Seo Contetnt writer
Instagram Influancer
Best 100 Seo Backlinks Just In 5$
90+ Da Backlinks
Product Content writing
Data Entry
Seo Content writer
ReplyDeleteThanks For Post which have lot of knowledge and informataion thanks.... VSDC Video Editor Pro Crack
ReplyDeleteI guess I am the only one who came here to share my very own experience. Guess what!? I am using my laptop for almost the past 2 year!!! but I had no idea of solving some basic issues. I do not know how to Crack Softwares Free Download But thankfully, I recently visited a website named vsthomes.com
Office Tool Plus crack
Soothe 2 VST crack
Revo Uninstaller Pro crack
IObit Smart Defrag Pro crack
progeCAD crack
ReplyDeleteI guess I am the only one who came here to share my very own experience. Guess what!? I am using my laptop for almost the past 2 year!!! but I had no idea of solving some basic issues. I do not know how to Crack Softwares Free Download But thankfully, I recently visited a website named vsthomes.com
Gravit Designer Pro crack
DxO PhotoLab crack
Adobe Photoshop CC crack
Resolume Arena crack
Wondershare PDFelement crack
Best Software.
ReplyDeleteSparkbooth Premium
Microsoft Toolkit
Wondershare TunesGo
Movavi Slideshow Maker
ReplyDeleteI guess I am the only one who came here to share my very own experience. Guess what!? I am using my laptop for almost the past 2 year!!! but I had no idea of solving some basic issues. I do not know how to Crack Softwares Free Download But thankfully, I recently visited a website named vsthomes.com
Captain Plugins crack
Redshift Render crack
Lounge Lizard VST crack
Gravit Designer Pro crack
Hard Disk Sentinel Pro crack
ReplyDeleteI guess I am the only one who came here to share my very own experience. Guess what!? I am using my laptop for almost the past 2 year!!! but I had no idea of solving some basic issues. I do not know how to Crack Softwares Free Download But thankfully, I recently visited a website named vsthomes.com
NordVPN crack
AVG Secure VPN crack
Tenorshare 4uKey crack
WebcamMax crack
PanoramaStudio Pro crack
Helicon Focus Pro crack
I guess I am the only one who came here to share my very own experience. Guess what!? I am using my laptop for almost the past 2 year!!! but I had no idea of solving some basic issues. I do not know how to Crack Softwares Free Download But thankfully, I recently visited a website named vsthomes.com
ReplyDeleteEzdrummer VST crack
Visual Studio crack
NordVPN crack
NetBalancer crack
Wondershare Video Converter crack
StudioRack V11 crack
I guess I am the only one who came here to share my very own experience. Guess what!? I am using my laptop for almost the past 2 year!!! but I had no idea of solving some basic issues. I do not know how to Crack Softwares Free Download But thankfully, I recently visited a website named vsthomes.com
ReplyDeleteTeamVieweAVG Secure VPN crack
Windows 7 All in One ISO crack
Bandicut crack
Movavi Photo Manager crack
NordVPN crack
Easeus Partition Master crack
Thanks for this informative blog and for giving us an opportunity to share our views.
ReplyDeleteIceCream Screen Recorder full crack
Small Pdf Pro Crack
WhatsApp Bulk Sender Crack
Staruml Crack
hdd regenerator full version
Microsoft Office 365
ReplyDeleteI like your all post. You have done really good work. Thank you for the information you provide, it helped me a lot. I hope to have many more entries or so from you.
Very interesting blog.
crackpc4u.com
Turnitin Software Free Crack
adobe photoshop cs6 extended crack .dll files 32bit/64bit
ReplyDeletefl studio cracked games
easyworship tutorial
aomei partition assistant lite edition
Cinch Audio Recorder Crack
Sothink Logo Maker Pro Crack
yeah, This is great place where we collected such a nice informations. Thank you!
ReplyDeletemovavi-slideshow-maker-crack
ableton-live-crack-torrent
gitkraken-crack
Thanks for sharing this quality information with us. I really enjoyed reading. Will surely going to share this URL with my friends,
ReplyDeleteApartment Movers Lansing MI
You guys also try it for best moving services
RadioBoss
ReplyDeleteI am very impressed with your post because this post is very beneficial for me
Nice post
ReplyDeleteDeep Freeze Standard Crack
Bandicam Crack is a lightweight screen recorder for Windows that can catch anything on your PC screen as a great video.
ReplyDeleteLikewise, Bandicam with crack makes it conceivable to record a specific territory on a PC screen or catch an amusement
that utilizes the DirectX / OpenGL / Vulkan design advancements.
Bandicam keygen
Some major provisions of the Constitution 1990 in respect to child rights are Right to nationality (every child who is found within the Kingdom of Nepal and the whereabouts of whose parents are not known shall, until the father of the child is traced, be deemed to be a citizen of Nepal by descent), Right to nonimageranger pro edition
ReplyDeleteMiniTool Partition Wizard Professional Crack With Keygen Full Version Download 2022 MiniTool Partition Wizard prompts serial clients to monitor partitions and segments. Also check the written structure, configure the SSD segment.
ReplyDeleteautodesk-maya-crack
ReplyDeleteVery Informative & watchful content, You guys also try it
ReplyDeleteHouse For Sale Star ID
for best Relocation services
ReplyDeleteSoftbortits remove logo Patch can
convert files by saving the video in another format such as FLV, MP4 and MKV. This is convenient
because the user does not have to use another program to perform the action.
ReplyDeleteWow, amazing block structure! How long
Have you written a blog before? Working on a blog seems easy.
The overview of your website is pretty good, not to mention what it does.
In the content!
SmartFTP Enterprise Crack
Proteus Crack
Miracle Box Thunder Edition Crack
OutByte Antivirus Crack
I like your post style as it’s unique from the others. I’m seeing it on the page. Thank you for sharing it.
ReplyDeleteExpress VPN with Crack
It solved all my queries perfectly. Our HP Printer offline service is also offered to get your printer offline.
ReplyDeleteOur HP Printer offline service is also offered to get your printer offline.
uninstall-microsoft-office-crack/
I like your all post. You have done really good work. Thank you for the information you provide, it helped me a lot. Getcrack.co I hope to have many more entries or so from you.
ReplyDeleteVery interesting blog.
Broadgun pdfMachine Ultimate Crack
Nitro Pro Crack
Wise Program Uninstaller Crack